The following are instructions for manually patching all versions of VB 4.x.x for the patch released March 13, 2014.
Verify you have PHP 5.2.0 or higher before you make these changes. If you don't you will break the site by making these changes.
The version of PHP on your server is visible in the Admin CP in the table near the top of the page, under thew news.
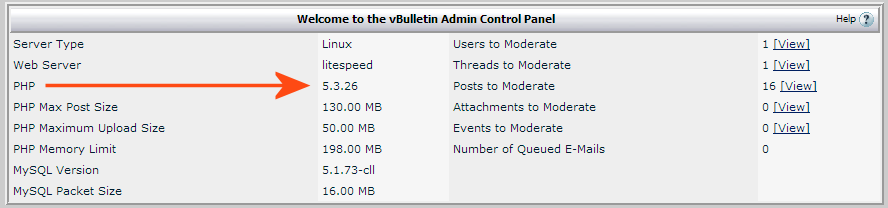
If your PHP version is not at least 5.2.0 see the announcement thread for more options.
Important - Some of the code boxes have a horizontal scroll bar, you will need to scroll to the right to see the entire line of code in these cases.
In includes/functions.php
Find the code:
Replace the line:
With:
In includes/functions_login.php
Find the code:
Replace the line:
With:
Finf the code:
Replace the line:
With:
In includes/functions_misc.php
Find the code:
Replace the line:
With:
Find the code:
Replace with:
In forumdisplay.php
Find the code:
Replace the line:
With:
In login.php (note- in some versions of 4.x this code does not exist, in that case ignore this step)
Find the code:
Replace the line:
With:
After editing each file upload it back to your server. Keep a backup of the old file just in case. If you ever need a backup of the original file you can re-download your version of VB 4.x from the Member's Area. Only vBulletin 4.2.2 will be officially patched in the Member's Area.
If you are on Windows use a dedicated code editor like Notepad2 or Notepad++ (both are free) to edit your .php files, do not use Windows Notepad.
Verify you have PHP 5.2.0 or higher before you make these changes. If you don't you will break the site by making these changes.
The version of PHP on your server is visible in the Admin CP in the table near the top of the page, under thew news.
If your PHP version is not at least 5.2.0 see the announcement thread for more options.
Important - Some of the code boxes have a horizontal scroll bar, you will need to scroll to the right to see the entire line of code in these cases.
In includes/functions.php
Find the code:
Code:
$postvars = construct_post_vars_html();
if ($vbulletin->GPC['postvars'])
{
$_postvars = @unserialize(verify_client_string($vbulletin->GPC['postvars']));
Code:
$_postvars = @unserialize(verify_client_string($vbulletin->GPC['postvars']));
Code:
$_postvars = array();
$client_string = verify_client_string($vbulletin->GPC['postvars']);
if ($client_string)
{
$_postvars = @json_decode($client_string, true);
}
Find the code:
Code:
}
if ($vbulletin->GPC['postvars'])
{
$postvars = @unserialize(verify_client_string($vbulletin->GPC['postvars']));
Code:
$postvars = @unserialize(verify_client_string($vbulletin->GPC['postvars']));
Code:
$postvars = array();
$client_string = verify_client_string($vbulletin->GPC['postvars']);
if ($client_string)
{
$postvars = @json_decode($client_string, true);
}
Code:
$postvars['securitytoken'] = $vbulletin->userinfo['securitytoken'];
}
$vbulletin->GPC['postvars'] = sign_client_string(serialize($postvars));
Code:
$vbulletin->GPC['postvars'] = sign_client_string(serialize($postvars));
Code:
$vbulletin->GPC['postvars'] = sign_client_string(json_encode($postvars));
Find the code:
Code:
}
else if ($vbulletin->superglobal_size['_POST'] > 0)
{
return '<input type="hidden" name="postvars" value="' . htmlspecialchars_uni(sign_client_string(serialize($_POST))) . '" />' . "\n";
Code:
return '<input type="hidden" name="postvars" value="' . htmlspecialchars_uni(sign_client_string(serialize($_POST))) . '" />' . "\n";
Code:
$string = json_encode($_POST);
return '<input type="hidden" name="postvars" value="' . htmlspecialchars_uni(sign_client_string($string)) . '" />' . "\n";
Code:
$temp = unserialize($serializedarr);
Code:
$temp = json_decode($serializedarr, true);
In forumdisplay.php
Find the code:
Code:
{
if (($check = verify_client_string($vbulletin->GPC['postvars'])) !== false)
{
$temp = unserialize($check);
Code:
$temp = unserialize($check);
Code:
$temp = json_decode($check, true);
Find the code:
Code:
exec_unstrike_user($vbulletin->GPC['vb_login_username']);
$_postvars = @unserialize(verify_client_string($vbulletin->GPC['postvars']));
Code:
$_postvars = @unserialize(verify_client_string($vbulletin->GPC['postvars']));
Code:
$_postvars = array();
$client_string = verify_client_string($vbulletin->GPC['postvars']);
if ($client_string)
{
$_postvars = @json_decode($client_string, true);
}
After editing each file upload it back to your server. Keep a backup of the old file just in case. If you ever need a backup of the original file you can re-download your version of VB 4.x from the Member's Area. Only vBulletin 4.2.2 will be officially patched in the Member's Area.
If you are on Windows use a dedicated code editor like Notepad2 or Notepad++ (both are free) to edit your .php files, do not use Windows Notepad.
Comment